Network & Security Solution.
Local Area Network Solution
A Local Area Network (LAN) is a private computer network that connects computers in small physical areas. Example A small office, A Single building, multiple buildings inside a campus etc. Wide Area Networks (WAN) is type of computer network to connect offices which are located in different geographical locations.
PSTN or Satellite medium are used for wide area network. But WAN’s ownership can be private or public. The speed of LAN is high(more than WAN). While the speed of WAN is slower than LAN.
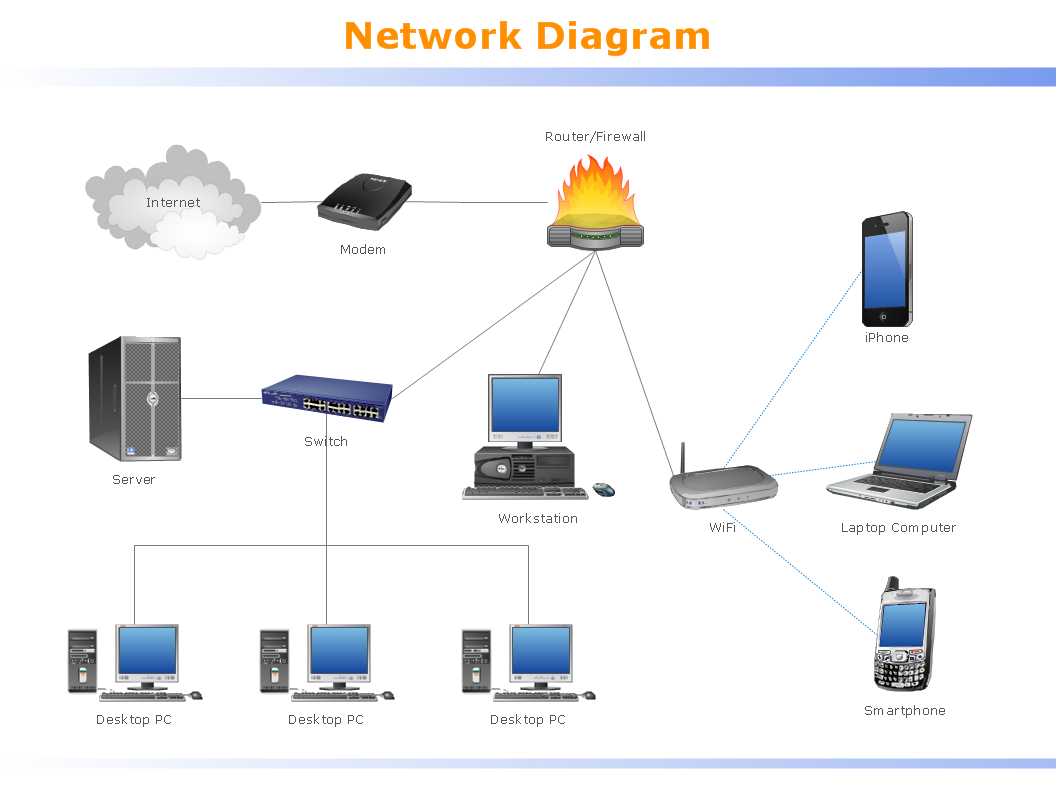
We offer to bring you a wide range of LAN services expanding the capability of desktop computers. We create a safe and reliable network environment for your office.
Our LAN services include provision, implementation, maintenance and management of LAN infrastructure equipment. While provisioning covers the selection, requisition and delivery of equipment to the customer’s premises, implementation includes equipment configuration, pre-implementation checks, installation and commissioning. Our maintenance service ensures support and fault rectification for installed equipment.
Wide Area Network Solution
A Wide Area Network (WAN) is a computer network that spans a relatively large geographical area. It normally consists of two or more Local-area networks (LANs). Computers connected to a WAN are often connected through the telephone system, DSL, leased lines etc.
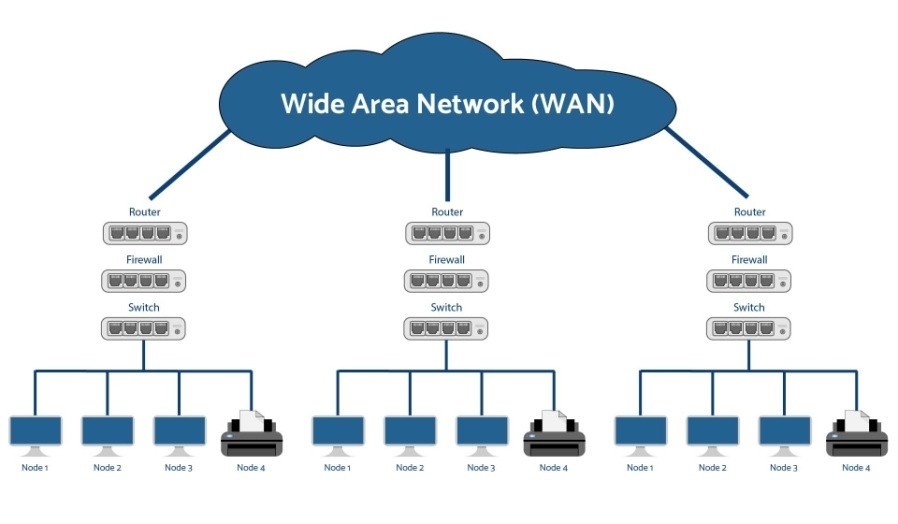
Our WAN solution enables multiple users and PCs to access the Data/ Internet network simultaneously through a single connection, facilitating a cost effective and optimized infrastructure. Access can be shared as information is obtained more rapidly.
Our WAN solution offers a large range of interfaces for Data & Internet access, so that link capacity can be adapted to a company’s needs. This allows voice & data to be sent across private IP networks in a compressed form, Frame Relay, Asynchronous Transfer Mode (ATM), ADSL Private Data Network, International Private Leased Circuits (IPLC) and public ISDN / PSTN networks.
Customers are provided with 24 x 7 monitoring of all their links, local and international – backed by our SLAs. Our Network Management Centre monitors all remote locations. We can provide factual reports to the customers.
Networking has become the most prominent area and commanding the focus for turnkey consultancy including design and implementation of enterprise networks and management solutions besides training and product support till end of life.
We have the necessary trained engineering resources to support leading products like HPE Network, Cisco, Huawei, Juniper, Avaya, and many more to provide solutions and services of very high standard to the clients.
By enabling high speed networks to become a strategic business asset, organizations can drive operational excellence to improve productivity, agility and business continuity. Organizations can develop logical segregation of network infrastructure by building VLANs as per applications like IP-based voice, wireless, multicast application, Inter-VLAN communication.
Active & Passive Network Components
Active networking is a communication pattern that allows packets flowing through a telecommunications network to dynamically modify the operation of the network. It also consists of active hardware, capable of routing or switching as well as executing code within active packets.
Passive network is a type of computer network in which each node works on a predefined function or process. Passive networks don’t execute any specialized code or instruction at any node and don’t change their behavior dynamically. Typically, this behavior is related to each network router node
Passive Network Components
Structured Cabling has become quite common for inter-connecting the various active devices in an IP network. So, the following passive components are commonly utilized in an IP Network for Structured Cabling.
- Cat 6/Cat 6a /Cat 7/Cat 7a UTP (Un-shielded Twisted Pair) Copper Cables– These are the network cables that connect a PC/ endpoint to a network switch. Sometimes, they are also used to provide inter-connectivity between switches if the distance is not greater than 90 meters, which is the distance they support for transmitting data without using any repeater (repeater function is provided by using network switches).
- Cat 6/Cat 6a /Cat 7/Cat 7a UTP Patch Cords– These are one meter/ 2-meter factory crimped cables with RJ-45 connectors installed at both ends. The Cat 6 Cables are not recommended to be directly terminated in either the network switch or the PC/endpoint. Only the patch cords terminate on both devices and connect to the Cat 6 Network cable through an I/O Box and UTP patch panel.
- I/O Box and Face Plate: The I/O Box and Face Plate are kept near the computers and a UTP patch cord is used to connect the Face Plate with the network port in the PC. The Cat 6/Cat 6a/Cat 7/Cat 7a UTP cable which comes from the switch terminates in to a permanent connection behind the I/O Box.
- UTP Patch Panel:The UTP Patch Panel is used for terminating all the Cat 6/Cat 6a/Cat 7/Cat 7a Cables that come from various PC’s/endpoints in the network (Actually I/O Box) to the rack. These Cables are permanently connected behind the UTP Patch Panel and UTP Patch Cords connect from the respective ports in front to the network switches. This allows for flexible moves, adds and changes without disturbing the switch ports. All the ports in the patch panel are labelled for easy identification of which node they are connected to.
- Optical Fiber Cables:For carrying data over 90 meters, Optical Fiber Cables are used. These cables use light for transmission of data instead of the electrical signals used by the UTP cables. They can carry data for longer distances – even to a few kilo meters without having to repeat the signals in between. There are two types of cables – Single Mode (Used for higher bandwidth requirements for longer distances) and Multi-Mode (Used for shorter distances). They connect directly to the Fiber Patch Panel at either end. Usually they come in multiples of 6 Cores – 6 Core, 12 Core, and 24 Core being common. For each connection, two cores are used – one for transmit and another for receive.
Active Network Components
We deal with industries most leading brands such as Cisco, D-Link, Dell, HP, Fortinet, Cyberoam, Gajshield, WatchGuard, SonicWall, Palo Alto, Check Point, Sophos, Quick Heal, Netgear, Aruba, Ruckus, Netgear, TP-Link, Broadcom, Extreme, Huawei, Nortel and many others for active components.We deliver all type of switches as per functionality, speed and ports you required.
Network Switches
- Unmanaged
- Managed
- Smart (or intelligent) switches
- Enterprise managed (or fully managed) switches
Layer 3 Switches/Chassis

Clients today need higher bandwidth, convergence, interoperability and scalability. Masinfosys offers switching solutions tailored to the needs of the customers.
We offer complete range of switching product portfolio from leading vendors like Cisco, HPE Aruba, Dell EMC, Netgear, D-Link, TP-Link, Huawei, Juniper, Broadcom, Extreme etc.
Routers
We use leading practices and proven methodologies to help clients deliver new capabilities and help integrate new technologies on routing platform. Today’s new generation Routers are capable of performing multiservice functions like Voice, Video, Data and other applications

We deliver complete range of routing product portfolio from leading vendors like Cisco, HPE Aruba, Juniper, Huawei etc
Wireless Network Solutions & Services
Wi-Fi is the name of a popular wireless networking technology that uses radio waves to provide wireless high-speed Internet and network connections. A common misconception is that the term Wi-Fi is short for “wireless fidelity,” however this is not the case. Wi-Fi is simply a trademarked phrase that means IEEE 802.11x
WiFi has quickly become a focal point of any business’ or organization’s network infrastructure. It allows users to efficiently work from tablets, laptops, and phones, while staying mobile and reducing infrastructure costs. Being freed from the desktop and empowered to work from anywhere within a business is a major advantage for any employee
Continue reading to learn about the benefits of WiFi networks, the features that drive their success, and how Mas Infosys can help create a perfect wireless deployment
We offer newer technology Wireless solutions with maximum speed & securely encrypted data seamlessly throughout entire office complex, industries, schools, colleges and university.
We offer leading industry Wi-Fi devices manufacturers like Cisco, Linksys, D-link, Aruba, Netgear, and TP-Link.
- Standalone
- Controller based
Aruba & Cisco Meraki Wifi Solution

We have the necessary trained engineering resources to support leading products like HPE Aruba Network, Cisco Meraki, Ubiquiti, MikroTik, EnGenius, Hawking technology many more to provide solutions and services of very high standard to the clients.
Solutions Offers:
- Assessment of the infrastructure and propose the low level design considering industry best practices.
- We use Cisco, HPE-Network Switches, Huawei & other product range to offer solutions for a design and successful solution implementation.
- Our expert resources will design, execute and manage the wireless networks. Mesh infrastructure deployments etc.,
- Outdoor & indoor uninterrupted wireless access solutions while roaming within campus or office premises.
- Structured Network Cabling (Copper & Fiber) Design & Implementation.
Network Cyber Security Solution
Network Security solutions aims to give eyes and ears for the customer company’s assets, ensuring early and instant warnings of failures in IT infrastructure, security breaches and changes in environmental parameters that may be critical. A skilled hacker can achieve unauthorized network access in a matter of minutes. Network Security blocks such intruders with encoding the contents of Data Packets against unauthorized access, and with Encryption for transmission over a public network.

We are specialized in cybersecurity services. We help clients focus on their core business while we take care of securing their information technology environment. We partner with leading technology providers to deliver transformational outcomes.
We have the necessary trained engineering resources to support leading products like Paloalto, Cisco, Shopos, Fortinet and many more to provide solutions and services of very high standard to the clients.
Network Firewall
A firewall is a system designed to prevent unauthorized access to or from a private network. You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized internet users from accessing private networks connected to the internet
Firewall protection has come a long way in recent years. In addition to monitoring internet traffic, the latest network firewall security products incorporate a wide range of additional features
We provide Best of Breed Security Devices like Firewalls and UTM from leading manufacturers like Cisco, SonicWALL, Fortinet, Cyberoam, WatchGuard, Palo Alto, Check Point, and Sophos with the below Features.
- URL/Web filtering
- IPS (Intrusion Prevention System)
- Anti-Virus
- Anti-Spam
- Application Filtering
- VPN (Virtual Private Network)
- High Availability (HA)
- ISP Load Balancing
DLP (Data Leak Prevention

Juniper Networks offers a portfolio of network firewalls that can service mid-size enterprises, large enterprises, service providers in a private or public cloud, and hybrid environments. Juniper’s Software-Defined Secure Network (SDSN) runs the JUNOS operating system, which provides uniform administration across its hardware-based and software firewalls.
Palo Alto Networks claims that some firewalls masquerade as next-generation firewalls by tacking deep inspection modules onto traditional port- and protocol-based architectures. It characterizes its own offering as true a NGFW that natively classifies all traffic based on applications, users and content.
Barracuda Networks NextGen Firewalls allow users to regulate application usage and prioritize network traffic with features like link balancing and WAN optimization. They can be deployed in cloud, virtual, and on-premises scenarios. This includes small remote offices, a single desktop, or a large campus. They can defend against: intrusion attempts and exploit patterns at the network layer; unauthorized access control attempts; DoS and DDoS attacks; malware such as viruses, worms and Trojans; and advanced threats such as backdoor attacks or covert phone home activity from botnets, as well as blocking access to unwanted websites and servers via web filtering.
Check Point Software‘s firewall gateway can be augmented via subscriptions to provide advanced malware protection and multiple threat intelligence feeds. Its firewall can support public clouds such as Amazon Web Services and Microsoft Azure. It also integrates with VMware NSX and Cisco Application Centric Infrastructure.
Cisco is one of the giants of the networking space, but it has also been steadily advancing its security capabilities. Its Adaptive Security Appliance (ASA) with Firepower services offers Sourcefire IPS, malware protection and application control.
SonicWALL has a range of firewall-related products for small offices and branches, midmarket and larger enterprises, and provides integration with wireless access points, WAN optimization products and switches.
Fortinet‘s Frigate product is used as a firewall for service providers, enterprises and SMBs. Its firewall appliances are said to accelerate packet processing.
Sophos XG Firewall integrates multiple security features into a single device to offer better network security. SOPHOS XG Firewall works at the gateway of the network and protects it from malware, vulnerabilities in web applications and sophisticated targeted attacks.
Antivirus – End Point Protection
Antivirus software, or anti-virus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses.Antivirus software protects against programs that corrupt computers and smartphones—and sometimes even steal their users’ identity.
Viruses used to be blocks of code that corrupted a single computer program then spread between users through sharing infected e-mail attachments. The virus landscape of today is far more complex and dangerous. Viruses can corrupt boot sectors, demand ransom payments, permanently embed themselves in the system memory, and more.
The Global Leader in IT Security is Bitdefender, the antivirus brand trusted by over 500 million users in 150 Countries. Bitdefender won numerous best antivirus from leading online testing labs including AV Comparatives, AV Test, PcMag and the Anti-Malware Testing Standard Organization.
Masinfosys Provide Client Compute End Point Security Solution using the below Antivirus Software to the Customer.
Bitdefender
Symantec Anti-Virus
McAfee Anti-Virus
Trend Micro Anti-Virus
Total AV Anti-Virus
Kaspersky Anti-virus
Avast

Antivirus programs are the essential line of defense against online cybersecurity threats. Using definitions and sophisticated behavior-recognition algorithms, they identify, quarantine, and safely remove threats from users’ operating systems.
Today’s viruses come in many different forms: Malware, spyware, adware, and rootkits are just some of the programs that promise to make users’ lives misery—and the list is growing by the year. Running a reliable antivirus software is the only way users can be sure that they won’t fall victim to a costly cyber-attack, have their device turned into a brick, or suffer potentially life-changing identity theft.
